Enterprise Services
Cyber Security
With technology enabling global connectivity with ease, it also brings in the associated risks with ease. Protection of highly confidential, sensitive and important information becomes the topmost priority for any customer and Geval6 comes in with its Security consulting practice to the rescue…
Overview
Feel secured and get peace of mind
From strategic advisory consulting, design and deploy services to cloud and managed security services, Geval6 has the expertise to help our customers stay ahead of cyber threats.
Our security services with innovative ideas enable customers to look at holistic needs and implement tamper-proof security solutions. Our experts with deep knowledge in proven frameworks can help in
-
Enterprise security strategy & governance and security audit
-
Vulnerability analysis & cyber defence
-
Ethical hacking & intrusion detection
Further we also have expertise in providing business continuity strategy, mobile security, data security, network defence, disaster recovery and preparedness, situation sampling & drill. Our pool of highly skilled Security professionals include over 150 members, 20 of them are high security cleared.
Our Offerings
Geval6’s offerings in the Security area are
Advisory
-
Our advisory service includes
-
IT Rationalization & Business Alignment Roadmap
-
Security Policy & Governance
-
Compliance & Technology Recommendation
-
M & A Impact analysis and Integration
Architecture & Audit
-
Audit would be the first step towards strengthening your security. Geval6 can
-
Formulate and review Enterprise Security Architecture
-
Perform audits covering Vulnerability and Cyber Exposure
-
Assess Compliance
Managed Service
-
We can take up security project either
-
On a turnkey basis
-
Provide highly skilled consultants
-
Our consultants have expertise to play the roles of a Security Architect, Data Security Specialist, Cyber Defense Analyst, GRC experts, Identity & Access management experts, Threat Analysts, Ethical Hackers and auditors.
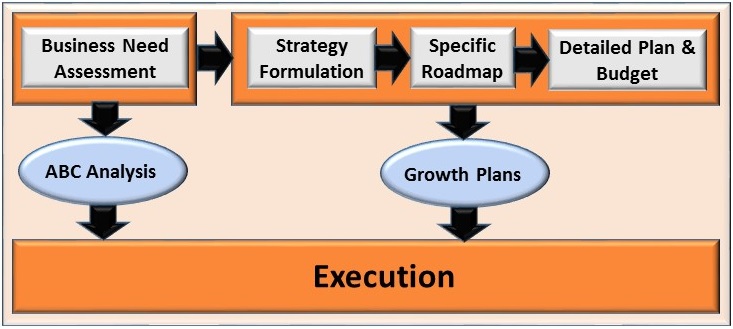
Our Process
The process we adopt in our security infrastructure and security advisory is depicted below
Steps involved in our approach are
-
Understand existing IT infrastructure and network traffic
-
Prepare security policy, processes and procedures
-
Perform ABC analysis to understand the priorities
-
Prepare a roadmap taking into account growth plans
-
Prepare detailed plan & budget for implementation
-
Execute the plan in a phased manner
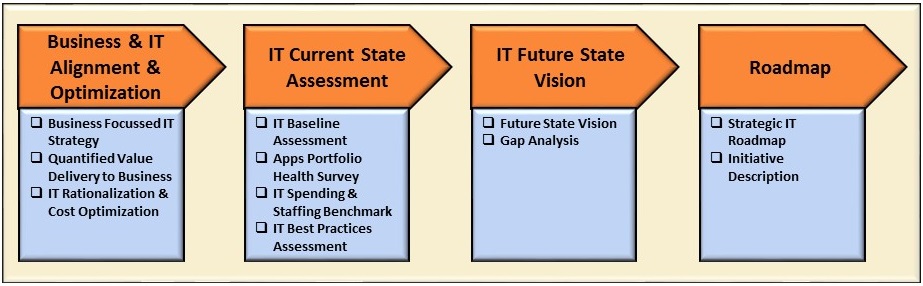
Our advisory activities can be further expanded into tangible deliverables. These include
-
IT Rationalization & Cost optimization
-
Current state assessment & best practices used for retention
-
Future requirements and Gap analysis
-
Roadmap document leading to implementation
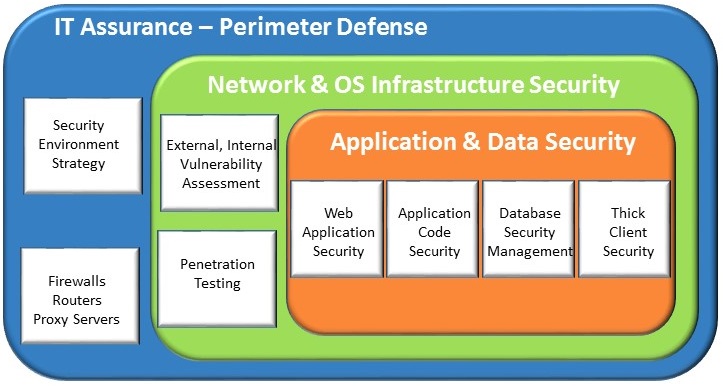
Defense is in depth. The security model that we implement will have multiple layers viz.,
-
Perimeter defense covering access from outside such as Firewalls, Routers, Proxy servers etc.,
-
Internal network and OS protection covering access privileges, security settings.
-
Application & Data security is the last layer and will have the most important business processes and information. Some measures include having server rooms, limiting access to external devices, controlling admin access etc.,
Our Technology Portfolio
![]() Identity & Access Management
Identity & Access Management
![]() Integrated GRC Management
Integrated GRC Management
![]() Threat Detection & Response
Threat Detection & Response
![]() Cloud Security
Cloud Security
*All Trade Marks belong to the respective owners
Our Team of Experts
Our team of experts consist of those who have “been there done that” kind of experience. Essentially these are “Doctors” for “IT Infrastructure”. They can detect problems based on symptoms as well as suggest preventive measures to avoid future problems.

